LDAP Configuration
Runtime gives admins the ability to use their local LDAP configuration to authenticate their users' access to the interface. This can be desirable, as this means that their credentials are synchronized, and you can manage their accounts from one central location. Starting in version 4.5 it’s also possible to import LDAP groups, and to use them in the Runtime user permissions system. This chapter of the manual looks into the configuration of the LDAP basics, and how to get the most out of this system. Currently, the group matching system is tuned to work with Active Directory setups, and as such varying results may be experienced when using another LDAP provider. In future updates, broader support for various LDAP platforms may be added.
LDAP Overview
In order to get to the LDAP menu, follow these steps:
Open Runtime
In the left-hand menu, press the User Management located under the Administration tab
In the User Management screen, navigate to the LDAP tab
You should now be greeted by the following overview:
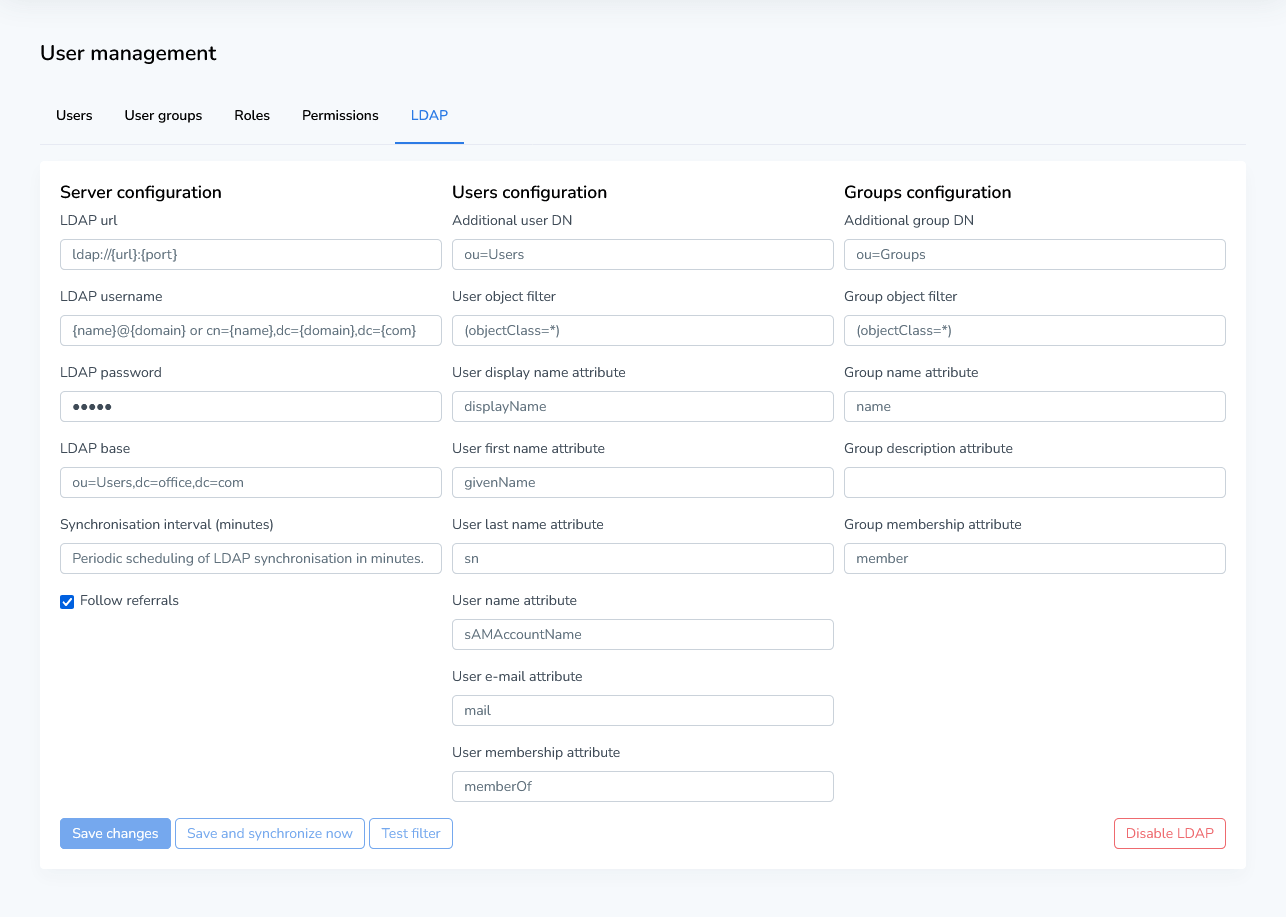
LDAP settings
Below is an overview of all the various fields the user can supply in order to import LDAP users. Currently, all values are required and must be filled. However, if a certain value does not exist within the LDAP environment (such as the user e-mail attribute), the user can supply a non-functioning attribute name. These values will then simply be returned as empty.
Server Configuration | Description |
|---|---|
LDAP URL | This is the URL you would use to connect to your LDAP environment. A correct example of this would be the following:
|
LDAP username | The username used to connect to the LDAP environment. Generally; this should be an administrator account or one with elevated rights. |
LDAP password | The password used to authenticate the user specified above against the LDAP environment. |
LDAP base | The LDAP base indicates a starting point from which we eventually start searching for user or group common names. This can be as wide or as narrow as you’d like. An example of this would be the following:
Everything below this specified base will be included in the coming searches. |
Synchronization interval (minutes) | After configuration this is the interval of how often the user data in Runtime is synchronized with what is specified in the LDAP environment. If this value is set to 0 no synchronization will occur unless the user manually does so by pressing the Save and synchronize now button. |
Users Configuration | Description |
Additional user DN | This value is attached to the LDAP base, and then used to search for users in the LDAP environment. It’s important to make sure that this value + the LDAP base lead to your user directory. An example of this would be the following:
This, with the example LDAP base would mean that Runtime searches for users in the following directory:
|
User object filter | This setting allows you to filter the resulting users from the above DN configuration based on variables. This can be any variable as provided by the LDAP environment on any given users. |
User display name attribute | This value from the LDAP environment will dictate what the user’s Display Name value in Runtime is. |
User first name attribute | This value from the LDAP environment will dictate what the user’s First Name value in Runtime is. |
User last name attribute | This value from the LDAP environment will dictate what the user’s Last Name value in Runtime is. |
User name attribute | This value from the LDAP environment will dictate what the user’s Username value in Runtime is. This is also the value the user will need to provide in order to log into Runtime. |
User e-mail attribute | This value from the LDAP environment will dictate what the user’s E-mail value in Runtime is. |
User membership attribute | This value will be used to check which groups this user belongs to. Generally, for Active Directory configurations this value refers to a variable that contains the full distinguished name of a given group. |
Groups Configuration | Description |
Additional group DN | This value is attached to the LDAP base, and then used to search for groups in the LDAP environment. It’s important to make sure that this value + the LDAP base lead to your group directory. An example of this would be the following:
This, with the example LDAP base would mean that Runtime searches for groups in the following directory:
|
Group object filter | This setting allows you to filter the resulting groups from the above DN configuration based on variables. This can be any variable as provided by the LDAP environment on any given groups. |
Group name attribute | This value from the LDAP environment will dictate what the group’s Name value in Runtime is. |
Group description attribute | This value from the LDAP environment will dictate what the group’s Description value in Runtime is. |
Group membership attribute | This value will be used to check which users this group contains. Generally, for Active Directory configurations this value refers to a variable that contains the full distinguished name of a user contained within this group. |
Save Changes:
This option saves the LDAP configuration as currently defined by the user. It creates or modifies theldap-config.jsonfile in theconffolder of the Runtime data folder. However, this action does not trigger a synchronization of LDAP credentials with Runtime.Save and Synchronize Now:
This option not only saves the LDAP configuration but also triggers an immediate synchronization of Runtime with the LDAP environment. Like the previous option, it creates or modifies the ldap-config.json file, but it also ensures that Runtime is synchronized with the LDAP system to reflect any changes.Test Filter:
This feature allows you to test the current LDAP filter configuration. By clicking the Test Filter button, Runtime fetches and displays the results based on the current configuration. The results are shown in two separate tables: one for groups and the other for users, making it easier to verify the LDAP configuration before applying it.
These options provide flexibility to manage LDAP settings and test the configuration to ensure it works as expected before making permanent changes or synchronizing with the environment.
LDAP Default values
As an extra resource, a table of default values for various LDAP implementations is included below. This can be used when configuring LDAP if the existing implementation uses standard LDAP settings.
Defaults | Active Directory | OpenLDAP | OpenLDAP (Read-Only Posix Schema) | Apache Directory Server | Apple Open Directory | FedoroDS | Generic Directory Server | Novell eDirectory Server | OpenDS | Generic Posix/RFC2307 Directory (Read-only) | Sun Directory Server Enterprise Edition |
|---|---|---|---|---|---|---|---|---|---|---|---|
User Object Class | user | inetorgperson | posixAccount | inetorgperson | posixAccount | posixAccount | inetorgperson | inetOrgPerson | inetorgperson | posixAccount | inetorgperson |
User Object Filter | (&(objectCategory=Person)(sAMAccountName=*)) | (objectclass=inetorgperson) | (objectclass=posixAccount) | (objectclass=inetorgperson) | (objectclass=posixAccount) | (objectclass=posixAccount) | (objectclass=inetorgperson) | (objectclass=inetorgperson) | (objectclass=inetorgperson) | (objectclass=posixAccount) | (objectclass=inetorgperson) |
User Name Attribute | sAMAccountName | cn | uid | cn | uid | uid | cn | cn | uid | uid | cn |
User Name RDN Attribute | cn | cn | cn | cn | cn | uid | cn | ||||
User First Name Attribute | givenName | givenName | givenName | givenName | givenName | givenName | givenName | givenName | givenName | givenName | givenName |
User Last Name Attribute | sn | sn | sn | sn | sn | sn | sn | sn | sn | sn | sn |
User Display Name Attribute | displayName | displayName | displayName | displayName | displayName | displayName | displayName | displayName | cn | displayName | displayName |
User Email Attribute | |||||||||||
User Password Attribute | unicodePwd | userPassword | userPassword | userPassword | userPassword | userPassword | userPassword | userPassword | userPassword | userPassword | userPassword |
User Unique ID Attribute | objectGUID | entryUUID | entryUUID | entryUUID | entryUUID | entryUUID | entryUUID | GUID | entryUUID | entryUUID | entryUUID |
Group Object Class | group | groupOfUniqueNames | groupOfUniqueNames | groupOfUniqueNames | groupOfUniqueNames | groupOfUniqueNames | groupOfUniqueNames | groupOfNames | groupOfUniqueNames | groupOfUniqueNames | groupOfUniqueNames |
Group Object Filter | (objectCategory=Group) | (objectclass=groupOfUniqueNames) | (objectclass=posixGroup) | (objectclass=groupOfUniqueNames) | (objectclass=posixGroup) | (objectclass=posixGroup) | (objectclass=groupOfUniqueNames) | (objectclass=groupOfNames) | (objectclass=groupOfUniqueNames) | (objectclass=posixGroup) | (objectclass=groupOfUniqueNames) |
Group Name Attribute | cn | cn | cn | cn | cn | cn | cn | cn | cn | cn | cn |
Group Description Attribute | description | description | description | description | description | description | description | description | description | description | description |
Group Members Attribute | member | uniqueMember | memberUid | uniqueMember | memberUid | memberUid | uniqueMember | member | uniqueMember | memberUid | uniqueMember |
User Membership Attribute | memberOf | memberOf | memberOf | memberOf | memberOf | memberOf | memberOf | groupMembership | memberOf | memberOf | memberOf |
Using LDAP over SSL
Every environment is unique, with varying operating system versions, types, and local variables. Consequently, some details in this guide may not fully align with your specific setup. This guide provides general instructions intended for Windows environments.
Please note that configuring SSL to enable HTTPS connections to DATPROF Runtime can be a time-consuming process. It requires familiarity with command-line tools and the ability to troubleshoot potential errors. Proceed only if you are confident in your ability to implement and manage these configurations.
Due to these complexities, the configuration and maintenance of SSL functionality fall outside the scope of DATPROF support.
LDAP over SSL is supported, but without configuration Runtime will return the following error:
[Root exception is javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target]
In order to use secure LDAP, you will need to import the certificate used for SSL into your JRE cacerts file. This file can be found in your runtime installation under runtime\jdk\lib\security. Copy your SSL certificate to this folder.
extending our path to include the keytool:
## By default, the keytool is not a part of PATH. We will need to add it.
set path=%path%;<your file explorer's path to the runtime folder>\jdk\bin
example:
set path=%path%;C:\Users\yoeri\Documents\DATPROF\Runtime\runtime-4.3.0\jdk\binNow that we can use the keytool, let's make the security folder our active directory.
Moving our current directory:
cd <your system path to the Runtime security folder>
example:
cd C:\Users\yoeri\Documents\DATPROF\Runtime\runtime-4.3.0\jdk\lib\securityYou can use the cacerts file to store your certificates.
The cacerts file is protected by a password. The default password of the cacerts file is changeit. You should change this password into your own password for security reasons!
Changing the keystore password:
keytool -storepasswd -keystore cacerts
Enter keystore password: changeit
New keystore password: new-password
Re-enter new keystore password: new-passwordNow, let's list the contents of our cacerts file.
Listing existing cacerts content:
keytool -list -v -keystore cacerts
enter keystore password:new-passwordYou should now see a large amount of text print. These are all the existing certificates in cacerts. Now, we'll add our certificate.
Importing our certificate into cacerts:
keytool -import -alias <the name of your certificate without its file extension> -keystore cacerts -file <the full file name of your certificate + extension>
example:
keytool -import -alias certificate -keystore cacerts -file certificate.crt
>Trust this certificate? [no]: yes
Certificate was added to keystore
Alternatively you can store your certificate elsewhere and supply a system path to this location for the -file command.After updating the LDAP settings in DATPROF Runtime with the correct connection strings, LDAP over SSL will be enabled. To apply these changes, you need to restart Runtime. This ensures that the new configuration settings are loaded and that LDAP over SSL operates correctly.
Don't forget to change your LDAP port to 636 (the default SSL port), and to change the LDAP URL in your Runtime configuration to start with ldaps:// instead of ldap://
