Applications
Runtime applications are generated packages from DATPROF Subset, DATPROF Privacy or DATPROF Integrate that contains all logic to execute a certain process like Data Masking, Subsetting, Generation and custom processes that are built and generated with DATPROF Integrate.
The central Application repository allows you to upload different applications in a central location, making them accessible across various environments. A single application can have multiple uploaded versions, which can be viewed by expanding the Application node and clicking on "All versions."
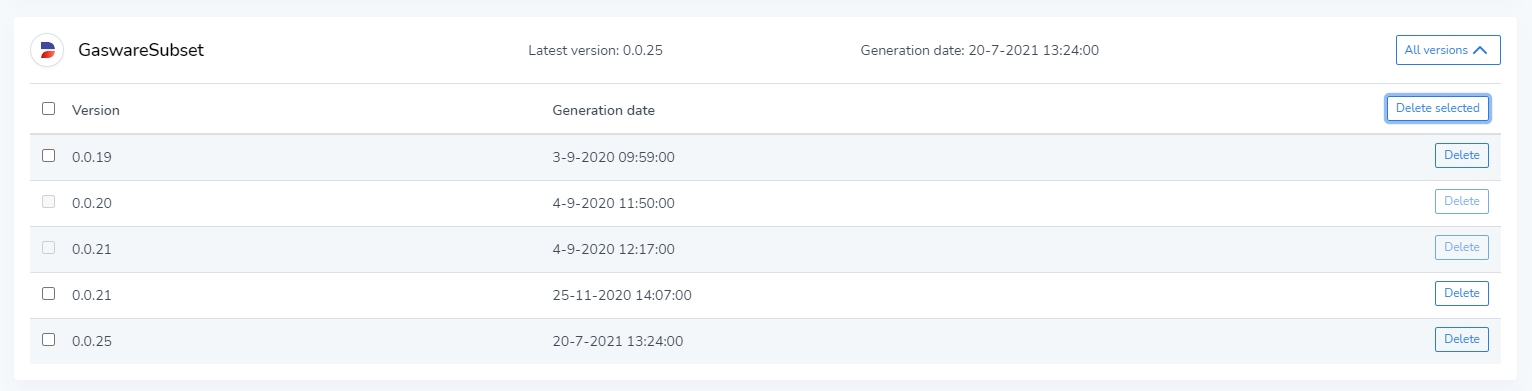
From this overview, you can also delete certain application versions. Applications that are currently installed in an environment cannot be deleted. Select one or more versions and click the "Delete selected" option to delete multiple versions at the same time.
Upload a new application
When you want to upload a new application, you can click on "Upload application" and select the generated ZIP file. Then, press "open". A second method is to just drag-and-drop a generated ZIP file into the Application overview. This will bring you to the Upload application view.
To actually upload and add the application to the repository, click on "Upload application".
If this version already exists in Runtime a warning will be generated. You can make a change in the version manually and click on "upload application" to proceed.

Application Verification
Given the potential inclusion of sensitive data and the inherent risks associated with executing actions that could disrupt system functionality, within Runtime it is now possible to enable “Application Verification”. By implementing robust encryption measures, organizations can safeguard sensitive information, mitigate unauthorized access, and reduce the likelihood of malicious tampering or unintended system disruptions. This approach not only enhances data security but also reinforces operational integrity, ensuring the safe and controlled execution of the Runtime processes.
Enabling Application Verification
To enable Application Verification, the configuration must be set up in Runtime and a security key must be retrieved from Privacy or Subset.
To enable Application Verification, you must change the runtime.properties file. This file is located in the conf folder within the Runtime data directory. Follow these steps to configure Application Verification:
Open the runtime.properties file using a text editor.
Scroll to the bottom of the file to find the Application Verification settings.
Locate the line starting with app.application-verification-mode= and update it to one of the following values based on your needs:
None: (Default) Runtime will not perform verification or display discrepancies.
Restricted: Only signed applications are allowed to be uploaded and deployed.
Warning: Packages are verified, and a warning is displayed if verification fails, but uploads and deployments are not blocked.
Save the file after making your changes.
Important: Restart Runtime to apply the updated settings.
Note on Restricted Mode
When Restricted mode is enabled, it applies only to applications uploaded after the mode is activated. Previously uploaded applications will not be checked or restricted, ensuring a smooth transition for existing deployments.
Retrieving a Security Key
Follow these steps to retrieve the security key from Privacy or Subset:
Open Privacy or Subset and navigate to the Help menu.
Locate and click on Show security key...
A window will appear displaying the Security Key.
Importing the Security Key in Runtime
This security key is essential for the verification process and must be imported into Runtime.
To import the Security key in Runtime, follow these steps:
Click on Security found in the Administration menu section in Runtime.
Click on Security keys.
Click on Add security key.
Import the security key generated by Privacy or Subset into this section.
Once the security key is imported, Runtime will be able verify the integrity of uploaded applications against the imported key, ensuring only authentic and unaltered applications are executed.
